# PLATFORM HTB# CTF NAME Compromised# DIFFICULTY Easy# CTF LINK https://app.hackthebox.com/sherlocks/CompromisedSCENARIO
Section titled “SCENARIO”Our SOC team detected suspicious activity in Network Traffic, the machine has been compromised and company information that should not have been there has now been stolen – it’s up to you to figure out what has happened and what data has been taken.
What is the IP address used for initial access?
Section titled “What is the IP address used for initial access?”162.252.{REDACTED}.54- if we filter HTTP, we can see the first request is made from
172.16.1.191towards54.172.252.161.in-addr.arpa. - however, the IP in the FQDN isn’t the actual destination IP. for that, we have to check the IP section of the frame.
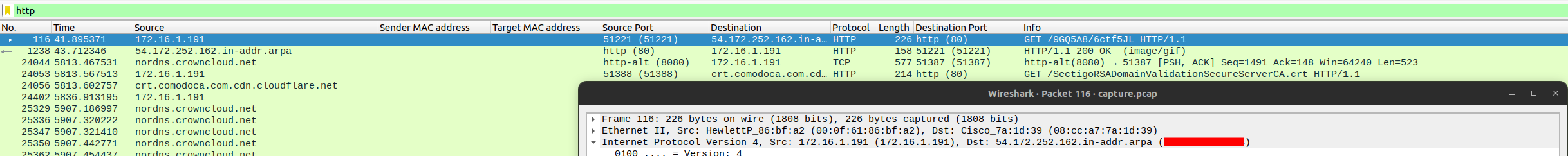
What is the SHA256 hash of the malware?
Section titled “What is the SHA256 hash of the malware?”- Save the file from
File->Export Objects->HTTP.
sha256sum /path/to/file9b8ffdc8ba2b{REDACTED}c3da6704e4d3c6What is the Family label of the malware?
Section titled “What is the Family label of the malware?”Pikabot- Found using the hash on VirusTotal.
When was the malware first seen in the wild (UTC)?
Section titled “When was the malware first seen in the wild (UTC)?”2023-05-19 14:01:21- Found using the hash on VirusTotal.
The malware used HTTPS traffic with a self-signed certificate. What are the ports, from smallest to largest?
Section titled “The malware used HTTPS traffic with a self-signed certificate. What are the ports, from smallest to largest?”2078, 2222, 32999- Filter for TLS/SSL traffic and check
Statistics->IPv4 Statistics.
What is the id-at-localityName of the self-signed certificate associated with the first malicious IP?
Section titled “What is the id-at-localityName of the self-signed certificate associated with the first malicious IP?”Pyop{redacted}rdium- Click on a
Certificate, Server Key Exchane, Server Hello Donepacket from Wireshark. - Expand on
Transport Layer Security->TLSv1.2 Record Layer->Handshake Protocol: Certificate->Certificates->Certificate: <id>->signedCertificate->subject - Take a look at the value for
RDNSequence item ... (id-at-localityName=SNIPPED)
What is the notBefore time(UTC) for this self-signed certificate?
Section titled “What is the notBefore time(UTC) for this self-signed certificate?”2023-05-14 {redacted} (UTC)- Click on a
Certificate, Server Key Exchane, Server Hello Donepacket from Wireshark. - Expand on
Transport Layer Security->TLSv1.2 Record Layer->Handshake Protocol: Certificate->Certificates->Certificate: <id>->signedCertificate->validity - Check value for
notBefore.
What was the domain used for tunneling?
Section titled “What was the domain used for tunneling?”ste{redacted}el.net- If we filter for DNS, we can see a lot of TXT queries to a particular domain.