# PLATFORM HTB# CTF NAME Reaper# DIFFICULTY Very Easy# CTF LINK https://app.hackthebox.com/sherlocks/ReaperSCENARIO
Section titled “SCENARIO”Our SIEM alerted us to a suspicious logon event which needs to be looked at immediately. The alert details were that the IP Address and the Source Workstation name were a mismatch. You are provided a network capture and event logs from the surrounding time around the incident timeframe. Corelate the given evidence and report back to your SOC Manager.
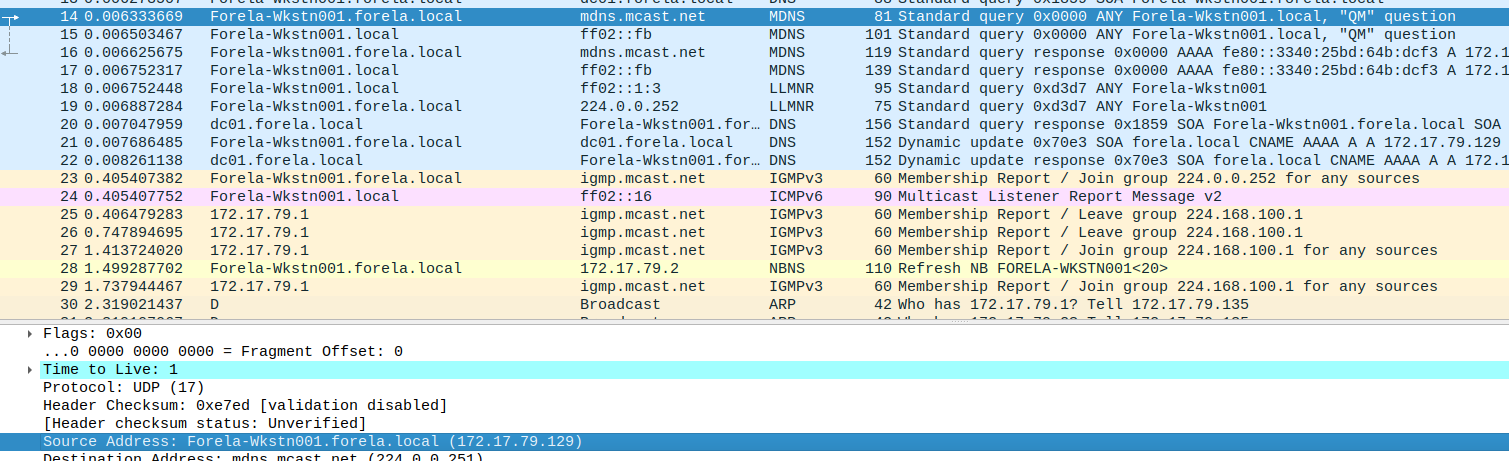
What is the IP Address for Forela-Wkstn001?
Section titled “What is the IP Address for Forela-Wkstn001?”- I clicked on a random packet that had
Forela-Wkstn001as source and I’ve inspected the Ipv4 information
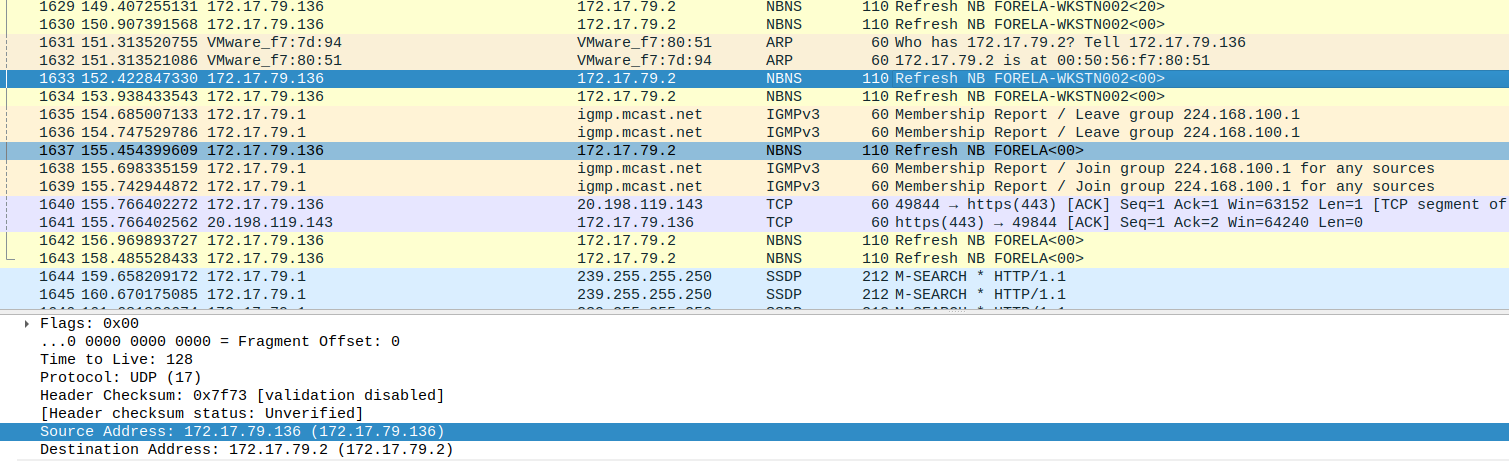
What is the IP Address for Forela-Wkstn002?
Section titled “What is the IP Address for Forela-Wkstn002?”- Same procedure as above.
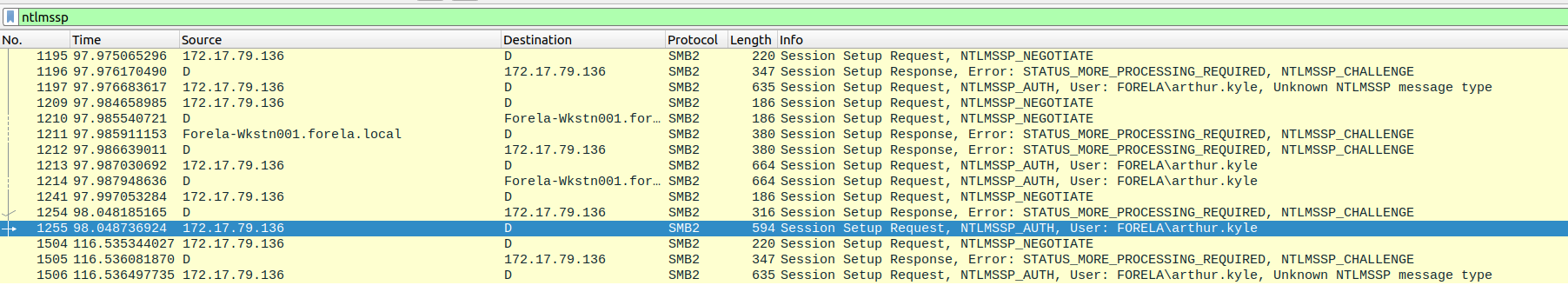
What is the username of the account whose hash was stolen by attacker?
Section titled “What is the username of the account whose hash was stolen by attacker?”- This can be found in wireshark by filtering by
ntlmsspprotocol or by having the source ip filtered after wkstn002’s IP.
What is the IP Address of Unknown Device used by the attacker to intercept credentials?
Section titled “What is the IP Address of Unknown Device used by the attacker to intercept credentials?”- Can be found by investigating the ARP protocol --- we can observe an ARP Flood attack
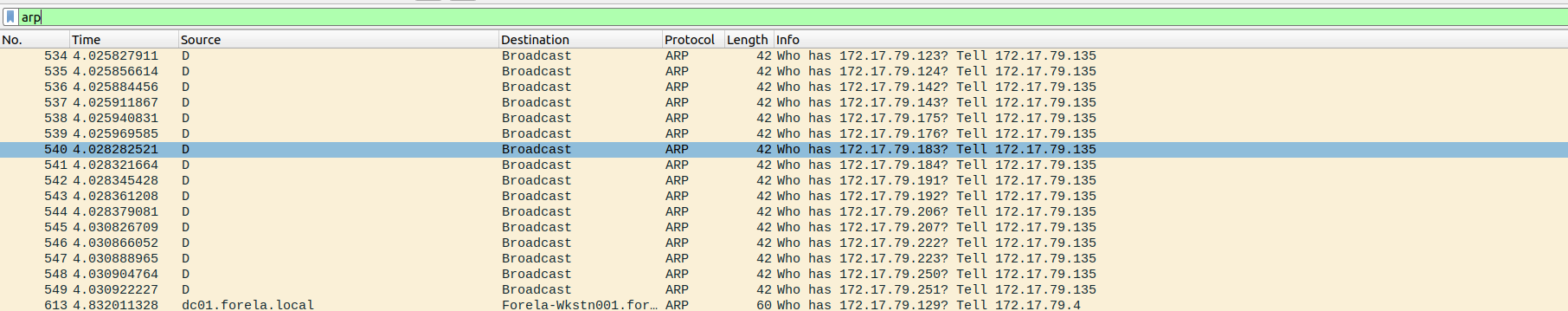
- All requests are being broadcasted by
172.17.79.135, so that’s the attacker’s device.
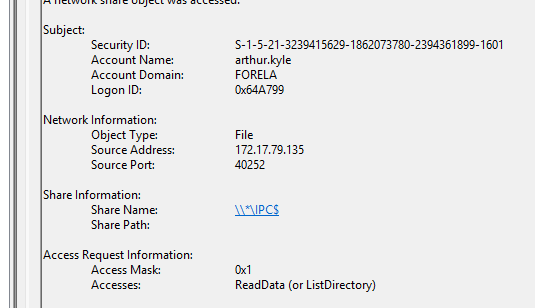
What was the fileshare navigated by the victim user account?
Section titled “What was the fileshare navigated by the victim user account?”- Can be found in Wireshark by filtering after
smb2protocol and analysing the traffic.
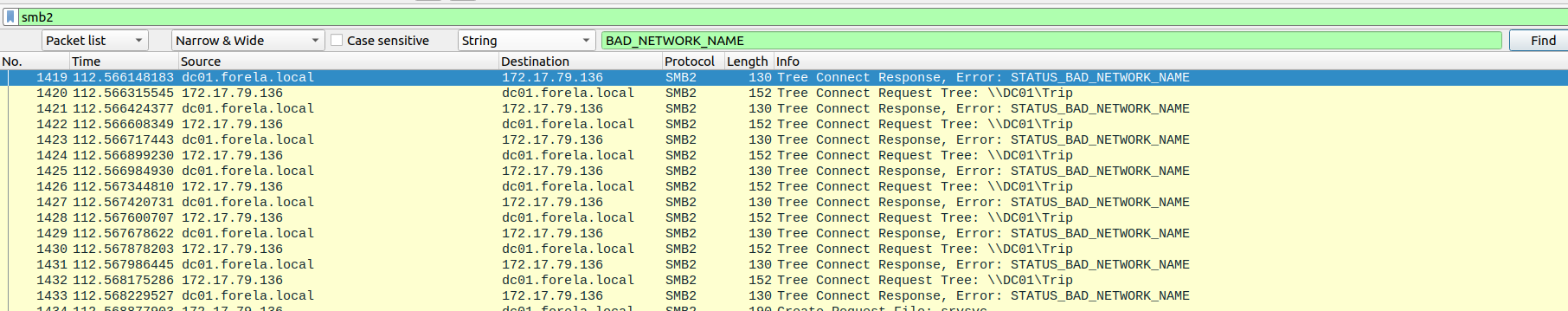
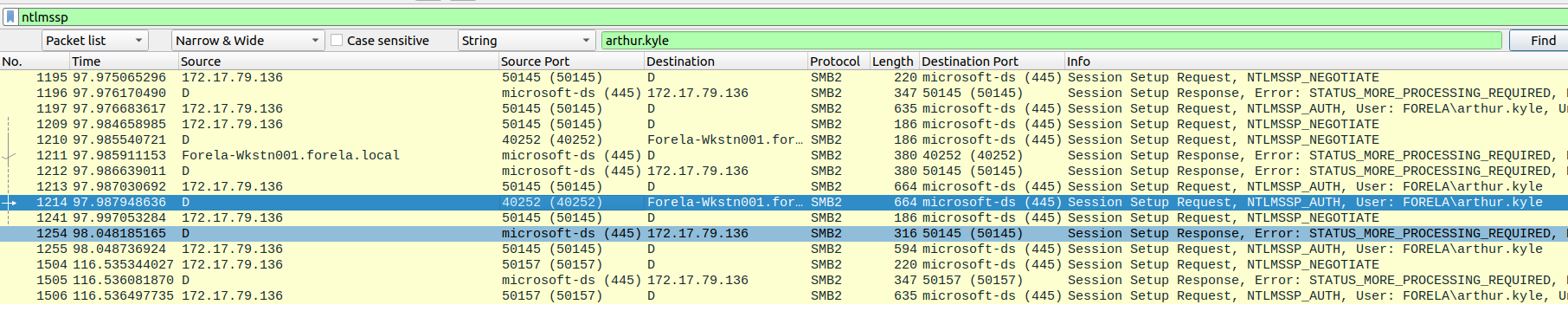
What is the source port used to logon to target workstation using the compromised account?
Section titled “What is the source port used to logon to target workstation using the compromised account?”- Filter again after
ntlmsspprotocol and search afterarthur.kyle. - Then, add the source and destination ports as columns in the view and then analyze the traffic for
NTLMSSP_AUTHentries that have as destination one of the workstations known.
What is the Logon ID for the malicious session?
Section titled “What is the Logon ID for the malicious session?”-
Open the .evtx file and filter after Event ID 4624.
-
The connection we found above is the entry that has
Logon Type: 3in the windows logs. -
The Logon ID is in the General Tab.
The detection was based on the mismatch of hostname and the assigned IP Address.What is the workstation name and the source IP Address from which the malicious logon occur?
Section titled “The detection was based on the mismatch of hostname and the assigned IP Address.What is the workstation name and the source IP Address from which the malicious logon occur?”- For the same event log found above, take a look at IpAddress and IpPort
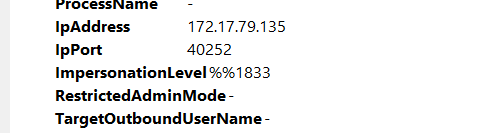
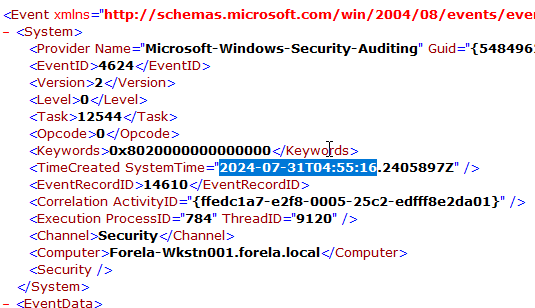
At what UTC time did the the malicious logon happen?
Section titled “At what UTC time did the the malicious logon happen?”- Same entry, check details tab in XML view.
What is the share Name accessed as part of the authentication process by the malicious tool used by the attacker?
Section titled “What is the share Name accessed as part of the authentication process by the malicious tool used by the attacker?”- Filter by Event ID 5140 - File Share.