# PLATFORM HTB# CTF NAME RomCom# DIFFICULTY Very Easy# CTF LINK https://app.hackthebox.com/sherlocks/RomComSCENARIO
Section titled “SCENARIO”Susan works at the Research Lab in Forela International Hospital. A Microsoft Defender alert was received from her computer, and she also mentioned that while extracting a document from the received file, she received tons of errors, but the document opened just fine. According to the latest threat intel feeds, WinRAR is being exploited in the wild to gain initial access into networks, and WinRAR is one of the Software programs the staff uses. You are a threat intelligence analyst with some background in DFIR. You have been provided a lightweight triage image to kick off the investigation while the SOC team sweeps the environment to find other attack indicators.
What is the CVE assigned to the WinRAR vulnerability exploited by the RomCom threat group in 2025?
Section titled “What is the CVE assigned to the WinRAR vulnerability exploited by the RomCom threat group in 2025?”- A quick “romcom winrar cve” on a search engine will disclose the CVE related to this vulnerability.
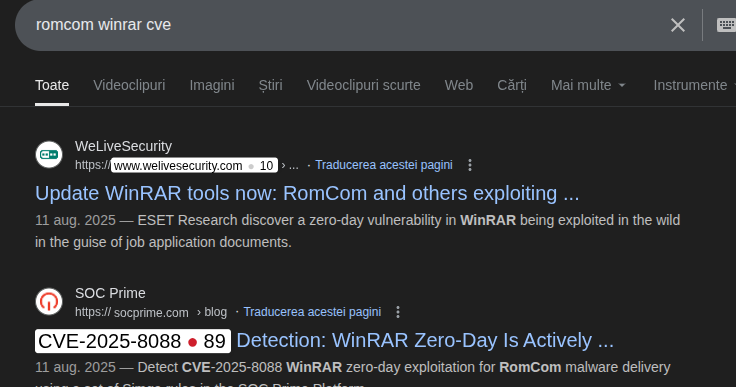
CVE-2025-8088What is the nature of this vulnerability?
Section titled “What is the nature of this vulnerability?”- By reading the article found found above we can find the answer to this question.
- On top of that, we can also gain insights about this exploit, its’ artifacts and insights into modus operandi.
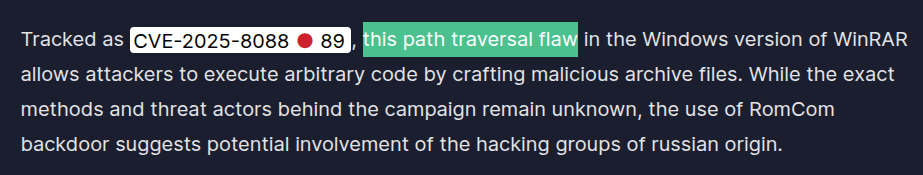
Path TraversalWhat is the name of the archive file under Susan’s documents folder that exploits the vulnerability upon opening the archive file?
Section titled “What is the name of the archive file under Susan’s documents folder that exploits the vulnerability upon opening the archive file?”- To visualize the files in Timeline Explorer (USN journal and MFT file), we need to first convert them to CSV. Below are the commands used to do this
MFTECmd.exe f- 'C:\Users\user\Desktop\RomCom\$MFT' --csv C:\Users\user\Desktop\RomCom --csvf MFT.csvMFTECmd.exe f- 'C:\Users\user\Desktop\RomCom\$Extend\$J' --csv C:\Users\user\Desktop\RomCom --csvf J.csv- Back to our CTF, if we CTRL + F the mft.csv file after
Susan\Documents, we find the following file(s).
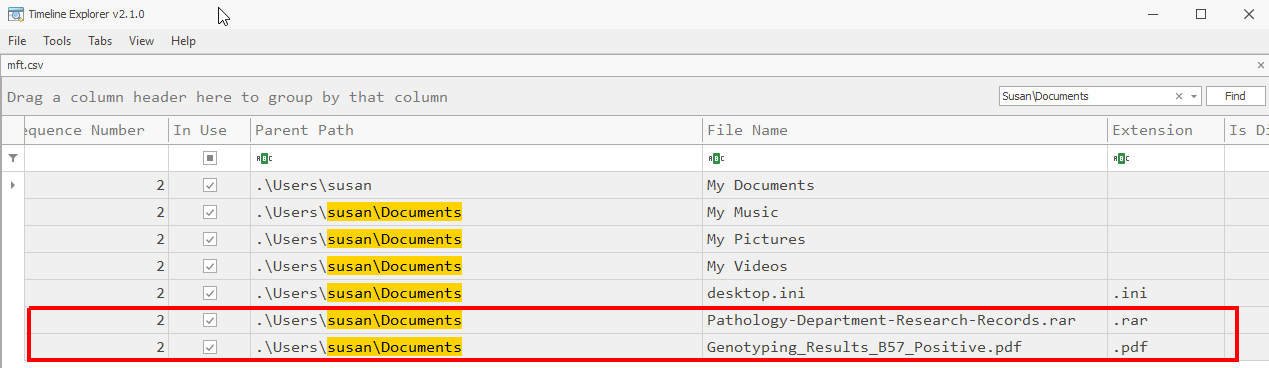
Pathology-Department-Research-Records.rarWhen was the archive file created on the disk?
Section titled “When was the archive file created on the disk?”- Scroll to the right on the entries found above and look at the
Created 0x10column
2025-09-02 08:13:50When was the archive file opened?
Section titled “When was the archive file opened?”- Same as above, just look at
Last Record Change 0x30column.
2025-09-02 08:14:04What is the name of the decoy document extracted from the archive file, meant to appear legitimate and distract the user?
Section titled “What is the name of the decoy document extracted from the archive file, meant to appear legitimate and distract the user?”- We can assume the answer to this file is the PDF highlighted in the screenshot from Q3 --- which was created at the (almost) same timestamp in the same directory.
Genotyping_Results_B57_Positive.pdfWhat is the name and path of the actual backdoor executable dropped by the archive file?
Section titled “What is the name and path of the actual backdoor executable dropped by the archive file?”- This can be found by checking either the MFT file or the USN Journal for file events around the known timestamp that the RAR archive was opened.
C:\Users\Susan\Appdata\Local\ApbxHelper.exe- We also know some known infection chains from the article above. More specifically, this paragraph seems to be valid for our case
Another infection chain causing the SnipBot malware variant distribution is triggered by launching via Display Settings.lnk, which runs ApbxHelper.exe (a tampered PuTTY CAC build with an invalid certificate). It checks for at least 69 recently opened documents before decrypting shellcode that retrieves more payloads from attacker-controlled servers.The exploit also drops a file to facilitate the persistence and execution of the backdoor. What is the path and name of this file?
Section titled “The exploit also drops a file to facilitate the persistence and execution of the backdoor. What is the path and name of this file?”- Same explanation as above. These two files (this one and the malware itself) are right next to each other in the MFT file if we sort on timestamps. Easy to correlate.
C:\Users\susan\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Display Settings.lnkWhat is the associated MITRE Technique ID discussed in the previous question?
Section titled “What is the associated MITRE Technique ID discussed in the previous question?”- I’ve googled after “MITRE start menu startup persistence” and landed on T1547 - Boot or Logon Autostart Execution page here.
- After a bit of searching around, I landed on a page describing our case here.
T1547.009When was the decoy document opened by the end user, thinking it to be a legitimate document?
Section titled “When was the decoy document opened by the end user, thinking it to be a legitimate document?”- For the PDF entry we found in Q6, check
Last accesscolumn in MFT file.
2025-09-02 08:15:05